Unattended upgrades in Debian – confirm blog
Ignored upgrades will (clearly) update your Debian-based system unattendenly. If we keep it basic, this is generally an automated apt-get upgrade with some tweaks. That’s it– that’s ignored upgrades!
Why should I utilize them?
Well, everything depends upon your environment and your patching behaviour and most likely your (business) procedures. I had some conversations with pals and clients of ours, and this is what I have actually heard up until now:
Pros for ignored upgrades
- You desire your systems constantly to be updated
- You desire your systems constantly to have the most recent security spots
- You do not wish to spot them routinely by hand
- Even if you miss out on the information of a brand-new vulnerability, you desire it to be covered
Cons for ignored upgrades
- You can’t do it, since your business business states you just have a couple of particular spot windows
- You understand your application breaks if you upgrade it instantly
- You wish to do whatever by hand, or a minimum of conjure up an automatic upgrade procedure by hand, so you have actually whatever under control
- You have actually a correct vulnerability management and do security upgrades based upon this
Never ever rely on a human
I’m more the let’s- do-it-unattended-guy, since IMHO this is the far better choice than the rest. I have actually likewise my concerns with the factors I have actually heard for the cons.
Let me begin with the (in my viewpoint) most apparent issue in declining ignored upgrades– the person. We’re bad in doing things correctly 100% of the time. We’re human beings and this becomes part of our nature– we’re not ideal and we make errors, this is how we find out and progress. However much more essential, we may have bad days, we’re under tension, we have actually a great deal of work, we go on holiday and we forget things. Now, what occurs if there’s a brand-new vulnerability and you’re simply missed out on or forgot it? What occurs if you’re on holiday, or you’ve method excessive work to even look into the most recent vulnerability? It most likely will not get covered (in time), and I believe all of us concur that this is actually bad! So simply trusting a human operator is a bad choice
Business business and their policies
As pointed out in the past, business business tend to specify spot windows, which generally indicates you can just update a particular server/ service in a particular time window. That isn’t extremely nimble, is it? You require to comprehend the inspiration behind this management choices. A great deal of individuals, specifically in management, hesitate of IT concerns, such as downtimes. Since of that, they’re terrified of modifications, and they begin to decline them. Never ever touch a running system, right?
However what if you can utilize that worry for your own benefit? What if you reveal them the drawback of this choice? What if you utilize their worry versus them? What if you state them something like:
So we have actually choice A, which indicates we await your charming spot window– which indicates our systems are susceptible up until that point– which indicates we can get hacked– which indicates that can damage the business– which indicates, naturally, somebody’s accountable for that little mishap– which indicates you may think of it when you’re going to sleep.
Then we have actually choice B, which indicates we do it instantly– which indicates our systems are constantly updated– which indicates they’re safe and secure– which indicates everyone’s pleased– which indicates you can go to sleep with a peace of mind.
Simply to be clear here, IMHO choice A (in basic) is the slowed down choice and just makes good sense in some exceptions. You need to definitly go for choice B.
Exceptions
Obviously, not every environment is as black & & white as explained here. I simply attempted to keep it a bit amusing. Still, you need to attempt to prevent human beings and do it instantly. Despite your choice, there may constantly be some exceptions. However that does not suggest you can’t do ignored upgrades for most of servers, services or bundles.
Getting it up & & prepared
Setup
Debian currently has a good documents about ignored upgrades. The documents is good and I utilized it to get it up & & running. Nevertheless, this is simply for the fundamental setup and I needed to determine the deets by myself.
So let’s begin by setting up the needed bundles:
apt-get set up unattended-upgrades apt-listchanges
- unattended-upgrades is doing the ignored upgrades (apparent, huh?)
- apt-listchanges reveals or sends by mail the modifications of a bundle prior to installing it
Setup
The setup files in concern are the following:
/ etc/apt/apt. conf.d/ 20auto-upgrades. / etc/apt/apt. conf.d/ 50unattended-upgrades. / etc/apt/listchanges. conf
To Start With the 20auto-upgrades file:
APT:: Routine:: Update-Package-Lists "1";. APT:: Routine:: Unattended-Upgrade "1";.
This generally states do an apt-get upgrade and apt-get upgrade every day, hence the number 1 ( n-days) as worth.
Successive, the 50unattended-upgrades file:
Unattended-Upgrade:: Origins-Pattern {
" origin= Debian, codename=$ {distro_codename}, label= Debian-Security";.
};.
Unattended-Upgrade:: Package-Blacklist {
};.
Now, in this file you have actually the option which bundles need to be updated. Debian currently discusses a lot in the default setup, which is:
// Lines listed below have the format format is "keyword= worth, ...". A.
// bundle will be updated just if the worths in its metadata match.
// all the provided keywords in a line. (To put it simply, left out.
// keywords are wild cards.) The keywords stem from the Release.
// file, however a number of aliases are accepted. The accepted keywords are:.
// a, archive, suite (eg, "steady").
// c, element (eg, "primary", "contrib", "non-free").
// l, label (eg, "Debian", "Debian-Security").
// o, origin (eg, "Debian", "Informal Multimedia Plans").
// n, codename (eg, "jessie", "jessie-updates").
// website (eg, "http.debian.net").
// The readily available worths on the system are printed by the command.
// "apt-cache policy", and can be debugged by running.
// "unattended-upgrades -d" and taking a look at the log file.
//.
// Within lines unattended-upgrades permits 2 macros whose worths are.
// originated from/ etc/debian _ variation:.
// $ {distro_id} Set up origin.
// $ {distro_codename} Set up codename (eg, "jessie").
Lastly, the listchanges.conf file:
[apt] frontend= pager. validate= incorrect. email_address= root. save_seen=/ var/lib/apt/ listchanges.db. which= news.
This is the file utilized to set up listchanges, which tracks modifications. Simply make certain your mail config is working and the e-mail address is specified properly.
Running it
unattended-ugprades is running instantly and is called by means of cronjob. You do not require to set up apticron or alike, as pointed out in a number of other posts.
If you wish to debug it, you can quickly run it on the CLI by means of:
unattended-upgrades -d
Logging
If you wish to know what was going on, examine the logfile found here:
/ var/log/unattended-upgrades/
You can likewise include the following setup to send you mails when an upgrade took place:
Unattended-Upgrade:: Mail "root";. Unattended-Upgrade:: MailOnlyOnError "incorrect";
How we do it
Our setup
For our facilities, we’re setting up and setting up unattended-upgrades instantly by means of Ansible on every server. Here’s our default setup with remarks.
20auto-upgrades:
//. //!!! CAUTION: This file is handled by Ansible, DON'T modify it by hand !!! //. // Enable ignored upgrades. APT:: Routine:: Allow "1";. // Do "apt-get upgrade" every n-days (0= disable). APT:: Routine:: Unattended-Upgrade "1";. // Do "apt-get upgrade-- download-only" every n-days (0= disable). APT:: Routine:: Update-Package-Lists "1";. // Do "apt-get upgrade-- download-only" every n-days (0= disable). APT:: Routine:: Download-Upgradeable-Packages "1";. // Do "apt-get autoclean" every n-days (0= disable). APT:: Routine:: AutocleanInterval "7";
50unattended-upgrades:
//.
//!!! CAUTION: This file is handled by Ansible, DON'T modify it by hand !!!
//.
Unattended-Upgrade:: Origins-Pattern {
" o= Debian, n=$ {distro_codename}, l= Debian-Security";.
};.
Unattended-Upgrade:: Package-Blacklist {
};.
// Instantly run "dpkg-- force-confold-- set up -a".
Unattended-Upgrade:: AutoFixInterruptedDpkg "real";.
// Do automated elimination of brand-new unused dependences after the upgrade.
Unattended-Upgrade:: Remove-Unused-Dependencies "real";.
// Install upgrades when the maker is shuting down rather of doing it in the background.
Unattended-Upgrade:: InstallOnShutdown "incorrect";.
// Instantly reboot if the file/ var/run/reboot-required is discovered after the upgrade.
Unattended-Upgrade:: Automatic-Reboot "incorrect";.
// Instantly reboot even if there are users presently visited.
Unattended-Upgrade:: Automatic-Reboot-WithUsers "real";.
// If automated reboot is made it possible for and required, reboot at the particular time.
Unattended-Upgrade:: Automatic-Reboot-Time "now";.
// Enable mail alerts.
Unattended-Upgrade:: Mail "<@confirm.ch";. Unattended-Upgrade:: MailOnlyOnError "real";.
// Enable logging by means of syslog.
Unattended-Upgrade:: SyslogEnable "real";.
Unattended-Upgrade:: SyslogFacility "daemon"; Security-related vs. non-security-related updates
As you can see, we instantly set up security-related updates every day in the background. This guarantees our systems get the most essential security spots. For the upgrade of every other bundle, we utilize an Ansible playbook which merely does a dist-upgrade with a little exception handling, followed by running all setup playbooks once again with a last reboot.
Display for reboots
We do not instantly reboot our systems, since we do not desire them to go totally down in the middle of the day. Obviously you can arrange it by specifying the reboot time (aside from now), however our method is a bit various.
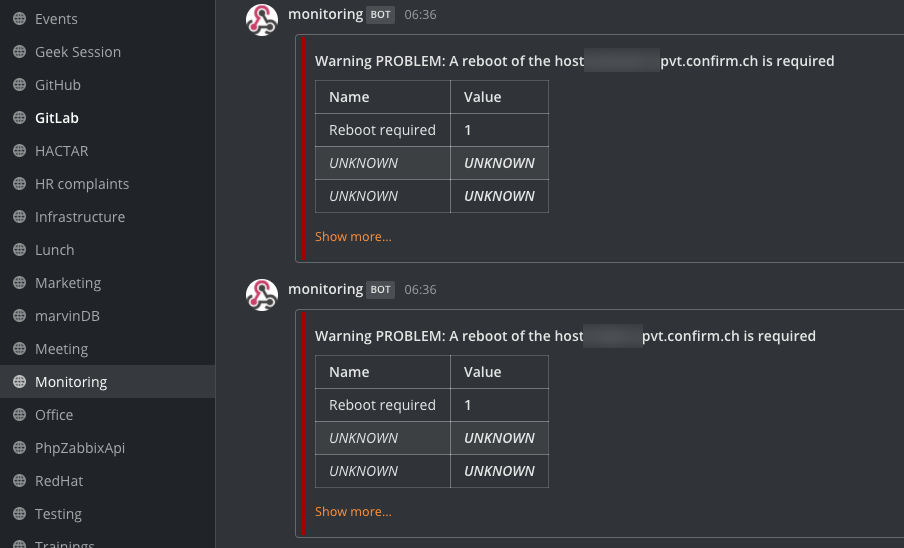
We merely keep track of for the / var/run/reboot-required file in our tracking and create an alert in Zabbix:
This produces a become our Mattermost tracking channel, so that everyone in our group learns about the “problem” and a reboot can be set up:
Decision
Integrating ignored security upgrades with automatic went to complete system upgrades is IMHO a good method to keep your environment updated and safe and secure, without losing control of crucial upgrades where a systems engineer is needed.
Source link

